- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Programming Languages / Perl
Perl
Perl
Great Reads
by Omar Al Zabir
Protect ASP.
by Oscar-Tark
If you are looking into white hat hacking,
by Oscar-Tark
In this article,
by anshulskywalker
Understanding of Example Based Machine Translation (EBMT) system and how to create your own using exisiting tools
Latest Articles
by Paul Aurelian Gagniuc
This article shows how to mix two signals into a third,
by Oscar-Tark
In this article,
by Oscar-Tark
A basic formatted string exploit shows you how small errors in programming with the printf function can be a lethal weapon for hackers looking to compromise a system.
by Shameel
Part 2 of this multi-part article series compares SQL Server and PostgreSQL article,
All Articles
30 Aug 2019 by Oscar-Tark
20 Mar 2022 by Paul Aurelian Gagniuc
This article shows how to mix two signals into a third, in variable proportions.
29 Feb 2020 by Oscar-Tark
4 Mar 2015 by rjdudley
6 Feb 2016 by John Jiyang Hou
6 Sep 2000 by Milan Gardian
16 Sep 2009 by cyber_flash
22 Dec 2011 by Kevin Schaefer
26 Aug 2013 by Rion Williams
5 Nov 2000 by Uwe Keim
12 Jul 2012 by Carlos Luis Rojas Aragonés
14 Mar 2008 by Helbrax
12 Nov 2002 by Khürt Williams
14 Nov 2004 by Kevin Staunton-Lambert
A general overview of Internet technologies including what the Internet actually is, what HTML and XML are, using Web forms, CGI/MIME, IIS ISAPI, ASP and creating HTML based front ends to databases via ODBC32, OLE DB, ADO and ASP.NET
13 Jan 2005 by kenearle
Tools to use HTML instead of plain text for supporting documents in Visual Studio.
25 Sep 2006 by fstrahberger
16 Jul 2007 by daluu
1 May 2009 by csrss
13 Apr 2009 by adminmyserver
12 Nov 2016 by Zebedee Mason
Perform dependency analysis by using Doxygen to parse source code and produce a report
7 Jul 2010 by logicchild
31 Aug 2002 by lexxwern
3 Nov 2004 by PixiGreg
A comprehensive Perl embedding solution.
2 Feb 2007 by alex turner
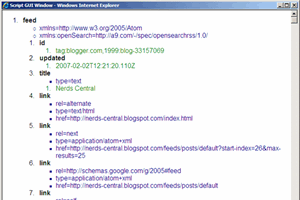
How to read an XML data source from file or AJAX and then represent it in Internet Explorer as a GUI
12 Apr 2006 by Michael Vasquez
13 Jun 2003 by John Aldrich
This article will detail a relatively simple method for generating a random alphanumeric string for using in the implementation of various cryptographic / security schema with PERL.
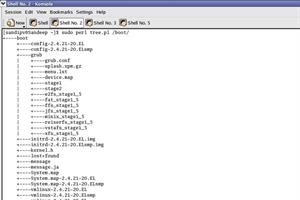
22 Apr 2008 by Sandeep_Vaniya
24 Mar 2004 by Jon Sagara