Here we discuss the installation of the operating system on Raspberry Pi, securing it, and configuring it for remote access over WiFi via SSH, RDP, and X from a Windows 10 machine.
Introduction
Traffic speed detection is big business. Municipalities around the world use it to deter speeders and generate revenue via speeding tickets. But the conventional speed detectors, typically based on RADAR or LIDAR, are very expensive.
This article series shows you how to build a reasonably accurate traffic speed detector using nothing but Deep Learning, and run it on an edge device like a Raspberry Pi.
You are welcome to download code for this series from the TrafficCV Git repository. We are assuming that you are Python and have basic knowledge of AI and neural networks.
In the previous article, we discussed the hardware components for our edge-computing project: Raspberry Pi 4, the ArduCam 5MP camera, and the Coral USB AI accelerator. This article will go through installation of the operating system on the Pi, securing it, and configuring it for remote access over WiFi via SSH and RDP from a Windows 10 machine.
Raspberry Pi OS
We’ll use the latest 32-bit version of Raspberry Pi OS (formerly Raspbian), which is based on the armhf Debian ARM port. 64-bit versions of the Raspberry Pi OS are available but the 64-bit support for Pi is still in the beta stage. Although 64-bit code should significantly improve performance in applications like OpenCV, in the prototyping stage, we care more about stability of our base components. After downloading, we’ll write the OS image to the 32GB microSD card from our LABISTS kit using the official Raspberry Pi Imager or a third-party imager like Balena Etcher.
We’ll need to connect a USB keyboard, mouse, and HDMI connectable monitor to the Pi to boot it up for the first time because remote access is disabled by default. We can then insert the card into the case slot (which exposes the Pi’s microSD slot) and switch on the power supply. The Pi has two status LEDs: red for power and green for microSD access. So, if everything is OK, you should see a steady red LED and a blinking green LED as the Pi boots up from its microSD card. There are many tutorials available for starting up Raspberry Pi for the first time, using the startup wizard, and troubleshooting bootup issues.
Security Considerations
There are reportedly 26.66 billion IoT devices active in 2020. Many of these devices are left unsecured and vulnerable to hacking and hijacking. Our system will be implemented by municipalities and local governments and deployed in public spaces, and will potentially have access to sensitive data and systems. Therefore, it is vital that we make security an essential part of our overall design. It’s the nature of IoT prototyping projects to not worry about securing devices until "later." In many cases, "later" never comes, and IoT devices are deployed publicly without basic security safeguards, presenting an irresistible target for hackers. Basic Raspberry Pi security is well documented in the "Securing your Raspberry Pi" post, and it’s recommended that we implement at least nine steps:
- Set a strong password for the default
pi user. This should be done when the Pi device starts up for the first time. - Disable auto login. By default, Pi will automatically login to the Pi’s LXDE desktop using the
pi user, but we should always require a password to be entered at login. - Disable Bluetooth. We don’t need the Bluetooth capabilities of the Pi 4 yet, so this should be disabled.
- Secure WiFi connection. Ideally, Pi should be connected to a WiFi router with basic security features enabled – like using WPA2-PSK authentication, not broadcasting its SSID, and using a MAC filter to restrict access to only known network devices. The Pi WiFi configuration is stored in the /etc/wpa_supplicant/wpa_supplicant.conf file, and it’s better to edit this file from the command line than rely on the
raspi-config tool. - Update your Debian installation with the latest packages and security fixes.
- Install a firewall on Pi. Remote access to services should only be allowed within a private subnet.
The ufw tool over the iptables firewall is very easy to use. You can add rules for essential network services, such as SSH, quite easily. Don’t assume your device will always be deployed behind a router.
- Change the SSH port to a non-standard one.
- Create a new user and use it for all development work instead of the default pi user. Disable SSH access for the
pi user. - Use key authentication only and disable password authentication over SSH.
A good rule of thumb for IoT device security is:
Always assume your device is exposed publicly on the Internet!
The short time we spend securing our device now could save us a large amount of embarrassment and financial costs in the future.
Access from Windows 10
SSH access to pur Pi can be enabled using the raspi-config and then secured as described above by editing the /etc/ssh/sshd_config file. Windows 10 has a decent Microsoft-provided OpenSSH client implementation, and we can use it to connect securely to the Pi device.
On our Windows 10 dev machine, we generate a new private-public key pair for connecting to Pi using ssh-keygen -t ed25519. We then have to add the public key to the authorized_keys file in our .ssh folder, and edit the config file to tell the SSH client we want to use that key pair for login into our Pi host.
If you have WSL on your Windows 10 machine, there’s a nice Linux command called ssh-copy-id that can copy the SSH keys for you, and also test that you can log into the remote machine using your key pair at the same time. Unfortunately, Windows 10 OpenSSH doesn’t seem to implement this yet. So, without WSL, you’ll have to append the public key line manually: echo ‘ssh-ed25519 ZZZ...mykey allisterb@myhost’ >> authorized_keys
The last step is to install xrdp on our Pi for remote desktop access from a Windows machine. Although VNC can also be used, xrdp offers a number of useful features – like a shared clipboard and access to local drives on the remote machine. Installing it on Pi is a relatively simple process with many tutorials like this one available.
Our Pi is now configured for remote access from our development machine via SSH and RDP with basic security safeguards. The final step in our system configuration is to install an X server on our development machine. This will allow us to run graphical applications, like OpenCV user interfaces, from Pi, and have them displayed as a local window on the Windows 10 machine. We used the open source VcXsrv project, and it had good compatibility with X clients on Pi. With this completed, we are ready to develop our computer vision and ML projects on the Pi device.
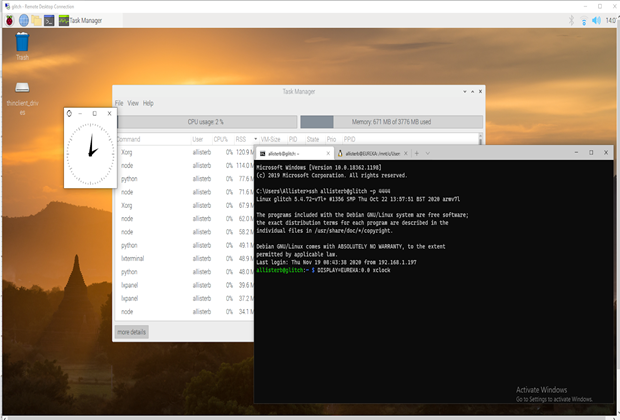
Windows 10 connected to Pi via SSH, RDP, and X
Next Step
In the next article, we’ll set up a development environment on Windows 10 for cross-platform computer vision and machine learning projects to run on our Pi device. Stay tuned!
I've been programming computers as a hobby and professionally for more than 20 years. I like both Windows and Linux. My current areas of interest are computer security, machine learning, conversational user interfaces, and .NET HPC.
