Background
Businesses face security, privacy and compliance challenges which are unique to the IoT. Security for IoT solutions includes ensuring that devices are securely provisioned, that there is secure connectivity between the devices and the cloud, as well as secure data protection in the cloud during processing and storage. An in-depth security strategy is needed to secure an Internet of Things (IoT) infrastructure.
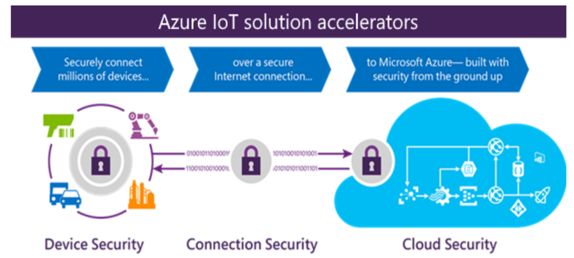
Securing an IoT Infrastructure
All of the actors and players involved with the manufacturing, development and deployment of IoT devices and infrastructure need to be involved in the development and execution of an effective security strategy.
IoT Hardware Manufacturer/Integrator
This includes manufacturers and integrators of hardware. The best security practices for IoT hardware manufacturers and integrators include:
- Scoping hardware to the minimum requirements: Additional features can open the device to attack, so only include the minimum features needed for the operation of the hardware. For example, only include USB ports if they’re essential for the device to have.
- Making hardware tamper proof: Devices should include built in mechanisms which can detect physical tampering with a device. Tamper signals can be uploaded to the cloud and checked frequently.
- Building around secure hardware: If possible, security features such as secure and encrypted storage, or boot functionality based on Trusted Platform Module (TPM) should be included.
- Making upgrades secure: Devices should have secure paths for upgrades to help ensure that devices remain secure before, during and after upgrades.
IoT Solution Developer
This is who develops an IoT solution. A developer can be in-house or a systems integrator who specialises in developing IoT solutions. The components of an IoT solution can be developed from scratch, include open-source components or use solution accelerators. The following are the best practices for IoT solution developers:
- Follow secure software development methodology: Security concerns influence the choice of platforms, languages and tools so it’s vital that security issues are considered and included from the inception of an IoT project
- Choose open-source software with care: An active community attached to open-source software means that the software is supported and that any issues are discovered and dealt with.
- Integrate with care: Ensure that all the interfaces of components being integrated are checked for security flaws.

IoT Solution Deployer
This involves deploying hardware in the field, ensuring the interconnection of devices and deploying solutions in hardware devices or in the cloud. Best practices for IoT solution deployers include:
- Deploying hardware securely: Devices may need to be deployed in unsecure locations. Therefore, it’s important to ensure that hardware deployment is as tamper-proof as possible; for example, securely cover USB or other ports.
- Keep authentication keys safe: Authentication keys and devices IDs for each device need to be kept secure. A compromised key can result in a malicious device masquerading as an existing device.

IoT Solution Operator
This includes the team who carries out long-term operations, monitoring, upgrades and maintenance and check that the system is functioning correctly. The following are the best practices for IoT solution operators:
- Keep the system up-to-date: All device operating systems, device drivers and operation systems need to be kept up-to-date in order to provide a secure operating system for the IoT devices.
- Protect against malicious activity: If possible, install the latest antivirus and malware capabilities on each device’s operating system.
- Audit frequently: Audit frequently for security-related issues. Event logging should also be reviewed frequently to check for security breaches.
- Physically protect the IoT infrastructure: Physical access to devices are often the source of the worst security attacks so it’s important to protect USB ports and other physical access to devices. Physical access can also be logged.
- Protect cloud credentials: Gaining access to an IoT system is most easily done through the use of cloud authentication credentials. Therefore, these credentials need to be protected; for example, by changing passwords frequently and not using these credentials on unsecure devices.
Device Capabilities
The capabilities of IoT devices can vary widely from computers to security cameras. Therefore, the security best practices can only be used in varying degrees. Manufacturers often include security and deployment best practice information which should also be followed.
Legacy Devices
Many devices in use may be unable to encrypt data, connect with the internet or provide auditing. In order to deal with these issues, a secure field gateway can be used to collect data from legacy and constrained devices, as well as providing many security features such as secure authentication and receipt commands from the cloud.
History
- 12th October, 2018: Version 1
Allen is CTO of SocialVoice (https://www.socialvoice.ai), where his company analyses video data at scale and gives Global Brands Knowledge, Insights and Actions never seen before! Allen is a chartered engineer, a Fellow of the British Computing Society, a Microsoft mvp and Regional Director, and C-Sharp Corner Community Adviser and MVP. His core technology interests are BigData, IoT and Machine Learning.
When not chained to his desk he can be found fixing broken things, playing music very badly or trying to shape things out of wood. He currently completing a PhD in AI and is also a ball throwing slave for his dogs.
